Cybersecurity and Malware Analysis with Automatic File Scanning Based on REMnux Tools
Project in Nutshell: We helped a telecom company automate their malware detection system with over 95% accuracy. Using open-source malware analysis tools, our client reduced project costs by 15%. With this solution and a regularly updated database, the company will save up to $1.5 million per year in response and remediation costs.
Client & Challenge
Our client, a leading European telecoms company, approached us to upgrade their malware threat detection system. The upgrade had two objectives:
- Implement automated malware analysis tools to reduce the need for ongoing involvement of their engineers, simplify the analysis of files for malware, improve efficiency and responsiveness.
- Set up performance verification and validate the reliability of their security measures by comparing their performance in preventing malware threats in cybersecurity with the results of public sandboxes.
Solution
1. Concept Development
To solve the client's problems, we offered a complete solution for cyber security and malware analysis based on REMnux, a Linux toolkit specifically designed for reverse engineering and deep malware analysis. This toolkit streamlines analysts, eliminating the need to hunt down, install, and configure various tools individually.
REMnux is powered almost entirely by open-source software, so this choice is optimal not only from the point of view of functionality, but it can also reduce the development time and budget.
2. Software Development
Our system comprises two core components: a sandbox and an environment for interacting with it.
- The sandbox runs on the Ubuntu distribution, equipped with the REMnux toolkit, deployed within a virtual machine environment.
- The environment includes a database of detected malware signatures and an API for seamless interaction with the sandbox.
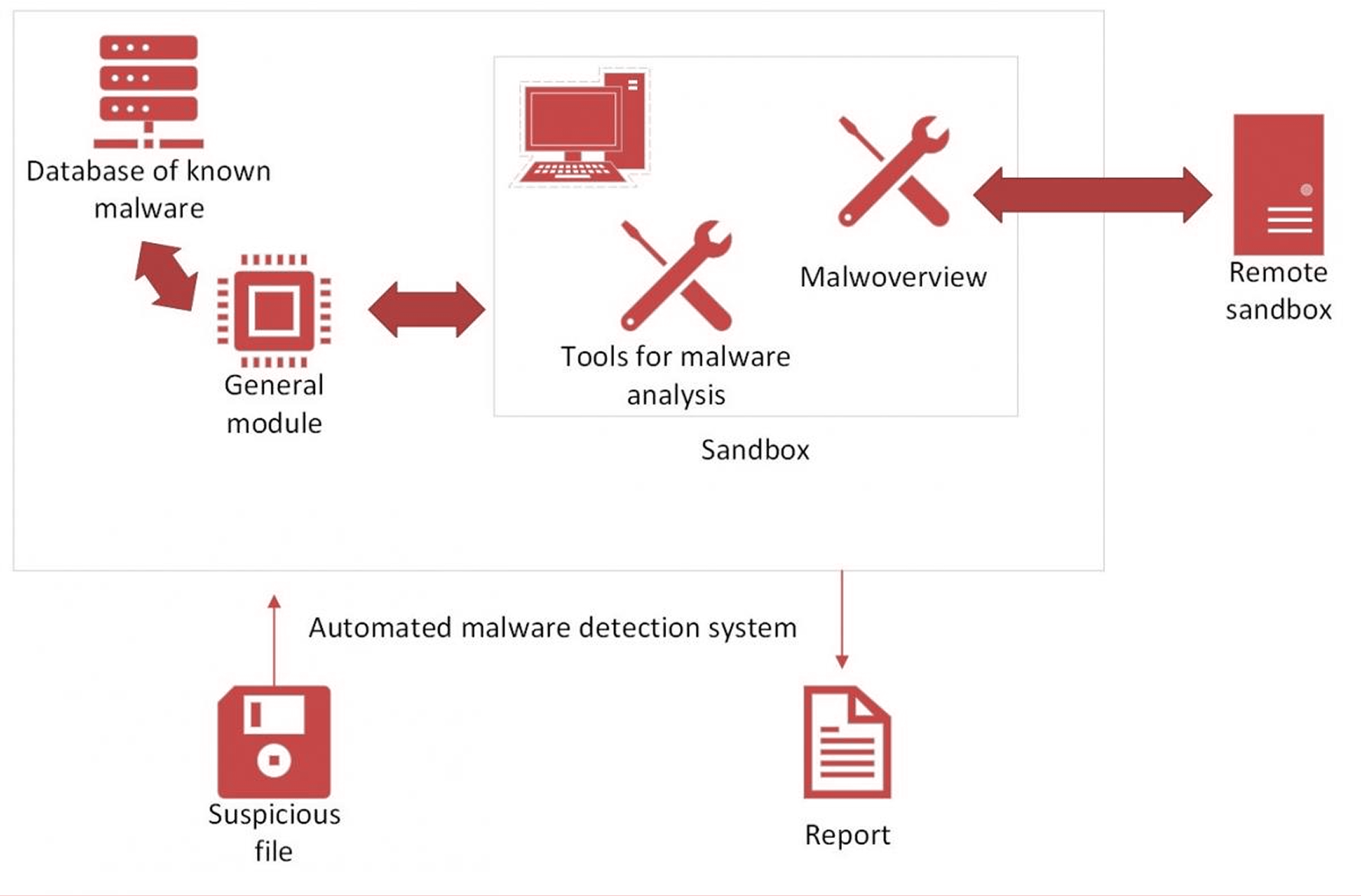
Block diagram of our automated solution based on open-source malware analysis tools
In addition to analysing malware with REMnux, we used several other tools:
- YARA Rules for creating descriptive profiles of malware families based on text or binary templates.
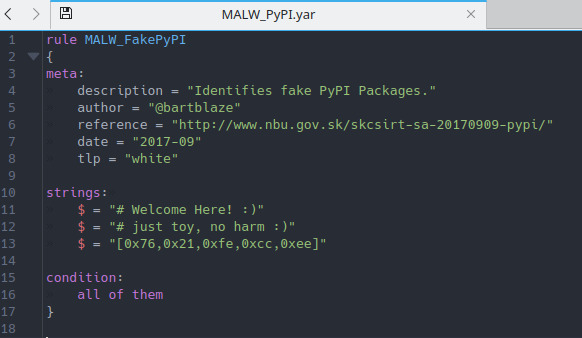
An example of YARA Rules
- Detect-It-Easy to detect file types.
- Malwoverview for initial and fast sorting of malware samples, URLs, IP addresses, domains, malware families, IOCs, and hashes. It works as a client for major existing sandboxes and can also receive dynamic and static behaviour reports, send and download samples from multiple endpoints.
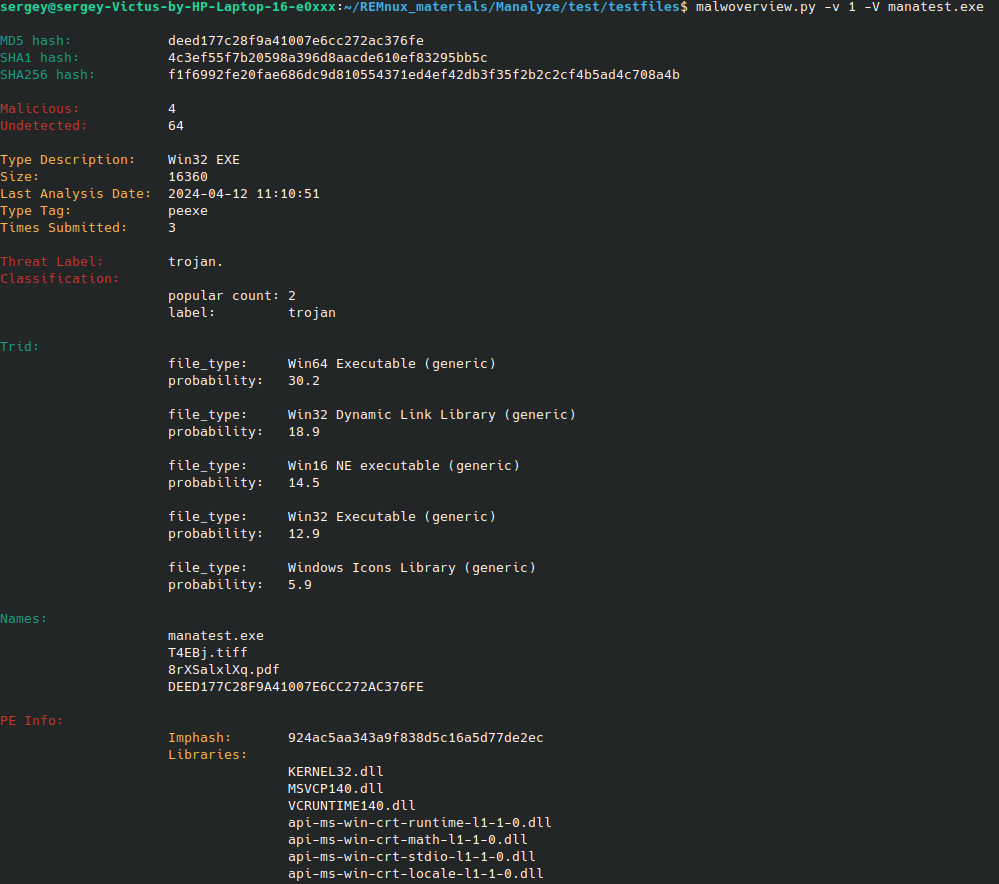
An example of how the Malwoverview works
- Manalyze for static PE file analysis for initial evaluation of an executable or set of executables. It collects weak signals that may indicate malicious behaviour and displays information that can help you find malware.
How automated our malware analysis tools work:
- When a suspicious file is identified, it undergoes initial scrutiny within the environment's database of known malware signatures.
- If the file is not flagged in the database, it is securely transferred via SSH to the sandbox for further analysis.
- Detect-It-Easy helps identify the file type and guides subsequent analysis steps.
- Based on the file type, the appropriate tools for deep malware analysis are selected. For instance, Windows executable files undergo scrutiny using Manalyze, while Microsoft Office files are analysed using ViperMonkey.
- If the initial analysis tools do not detect malware, the file is further scanned using Malwoverview, which can send files to remote sandboxes such as VirusTotal, Hybrid Analysis and others, providing comprehensive scanning across multiple platforms.
Business Value
Using open-source solutions to develop a deep malware analysis system, our client managed to reduce the project cost and accelerate the launch of the system. The project budget was 15% lower compared to a similar project that would have used proprietary solutions.
The implemented solution has significantly improved the detection and destruction of malicious software in the network security of our client and helped achieve the following results:
- Detection accuracy was over 95%, and false positives were reduced compared to traditional antivirus software.
- Time spent manually analysing files was reduced from 20 to 4 hours per week.
- Projected savings of approximately US$1.5 million per year in incident response and recovery costs.
More of What We Do for Cybersecurity
- Security Operations (SecOps): learn more about our security assurance and security testing services for your telecom projects.
- Security Scanning: a case study on testing WiFi access points for vulnerabilities and password cracking using Aircrack-Ng.
- VPN Solutions: explore our engineering expertise in developing secure VPN solutions and applications.






