Cybersecurity by design

Cybersecurity
Cyber threats are evolving, and non-compliant products face more than security breaches — regulatory fines, reputational damage, and market access restrictions.
At Promwad, we strengthen your solutions by:


Denis Petronenko, Head of Telecommunications Unit at Promwad
We follow the MITRE framework and deliver:








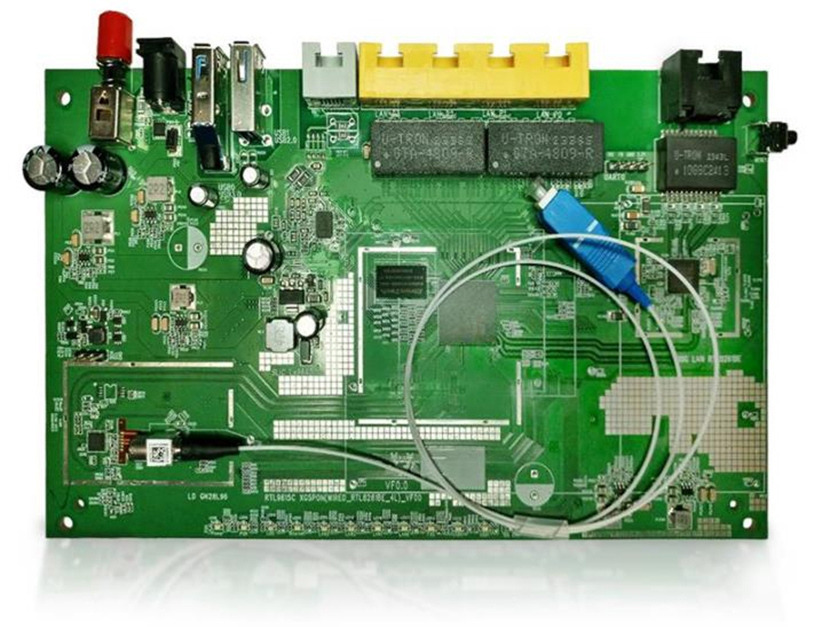
We audited a router based on the Realtek RTL9615C platform running OpenWRT/prplOS:
Compliance ensured with:
GDPR | FIPS 140-2 | Cyber Resilience Act | UL 2900-1
We tested an industrial switch based on the Microchip VSC7448YIH-01 chip for threat resistance. The project involved risk analysis, hardware/software security enhancements, and network protection:
Compliance ensured with:


















For maximum defence, we strengthen every layer of your infrastructure, including:
“As a result of collaboration, Promwad successfully delivered the first product. The team regularly held weekly meetings to discuss feedback and utilised email for follow-ups. Furthermore, they were knowledgeable in providing solutions.”
“The collaboration with Promwad has been successful, helping the client streamline their efforts and deliver work on time. The team is dedicated to meeting deadlines and working within the budget. Their communicative, available approach makes them easy to work with.”
“Promwad has strong capabilities to deliver project assets according to agreed-upon milestones, especially for projects where the shipment date cannot be changed. Their technical competence in Android AOSP was impressive. Promwad's technical manager/PM provided overall project status and deliverables in time via Scrum process setup.”
Cybersecurity by design
Security DevOps
Integrate security into your development pipeline from day one. We automate compliance, detect vulnerabilities early, and ensure secure code deployment without slowing down your release cycles.
Sociotechnical testing
Vulnerability scanning
Threat analysis
Specify, prioritise, and eliminate potential threats before they damage your systems. Our experts simulate real-world attack scenarios to uncover weak points and reinforce your defences.
Device & service compliance audit
Network penetration testing
Network Traffic Analysis
Encryption Testing
Configuration Review

Telecommunications
Automotive
IoT & consumer electronics
Hardware threat model, physical inspection, schematic & PCB review, secure boot, encryption algorithms in hardware , components protection from unauthorised access
Software threat model , SBOM (software bill of materials) , secure updates, patch management , CVE & CWE analysis, firmware scanning for vulnerabilities
Firewalls, VPN, anonymizers, DPI, proxy
GDPR , Cyber Resilience Act , NIST SP 800-53 , AES-256 , SSL, TLS , IEC 62334 , MISRA C, MISRA C++ , UL 2900-1, FIPS 140-2, ISO/IEC 7816 , PCI DSS, SEI CERT C Coding Standard
NIST-compliant hardware-based crypto , tamper-resistant chips , secure storage, NIST SP800-90B-compliant true random number, generator, authenticators: I2C, 1-wire, NFC
Drop us a line about your project! We will contact you today or the next business day. All submitted information will be kept confidential.