
DPI
Solutions
Custom DPI Software Development
Deep Packet Inspection (DPI) software helps improve network security and performance by controlling the content of data packets. With our vast expertise in DPI network monitoring and security, our experts can guide you through the selection of an ideal solution for your business needs.
At Promwad, we have a proven track record of successful implementation of custom DPI software across diverse platforms, including on-premise appliances, virtual machines, and cloud-based services, all while ensuring seamless integration and enhanced network security for our clients.
DPI: Improving Traffic Management and Analysis
Network traffic inspection, known as DPI, is a real-time examination method, which allows you to detect and prevent network security threats. DPI analysis helps to review the entire data packet, including the header and payload, in order to identify malicious traffic.
![]()
Optimising network resources
![]()
Enhancing security
![]()
Improving user experience
![]()
Monitoring infrastructure performance
![]()
Providing enhanced network visibility
![]()
Reducing costs through efficient resource allocation
Кey Functions of DPI
- Network traffic analysis
- Packet capture
- Protocol decoding
- Signature-based analysis
- Behavioural analysis
- Access control and strong authentication
- Traffic management: filtering and redistribution
- Application identification
- Intrusion detection and prevention
- Regulatory compliance monitoring
- Traffic classification
- Metadata extraction
- Flow analysis
- Session reconstruction
- Pattern matching
- Anomaly detection
- Heuristics
- Content-based analysis
- Statistical and payload analysis
- SSL/TLS decryption
- Network visualisation
- Network telemetry
- Quality of Service (QoS) monitoring
Our Case Studies on DPI Solutions

Smart router for content filtering
Commissioned by our client, we developed intelligent content-filtering routers that offer numerous features that enhance security and control:
- Phishing site blocking
- Parental control
- Anti-tracking
- Privacy protection
- Secure DNS
- Ad blocking
→ Read more about this case study
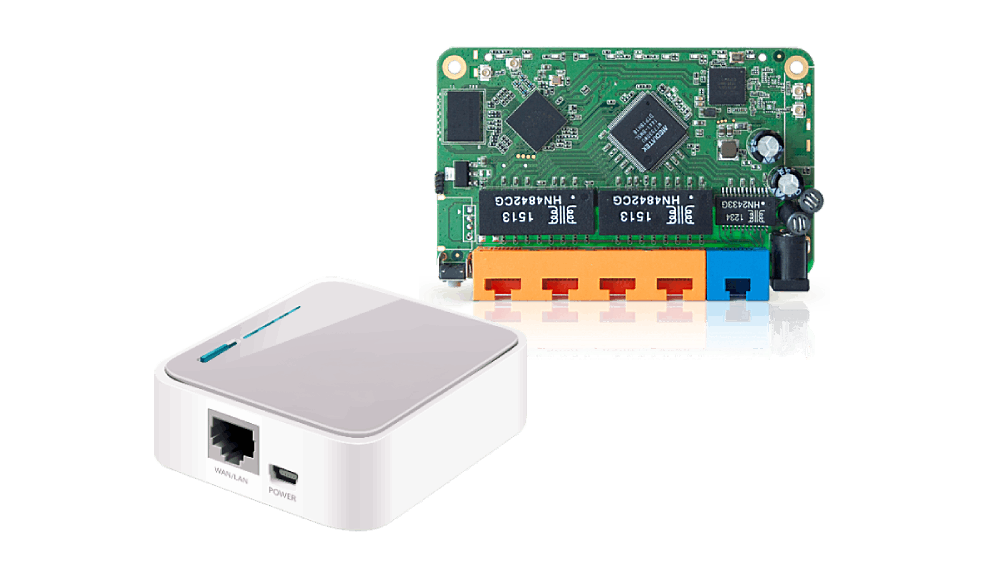
Network probe
By porting OpenWRT to wireless network devices, we assisted our client in verifying the quality and enhancing the user experience through the following functions:
→ Read more about custom OpenWRT in our projects
- Checking the connection speed and quality
- Identifying unauthorised access points
- Detecting interference on channels
- Identifying overloaded networks or channels
- Testing performance
- Identifying areas with poor coverage
Our Tech Map in DPI
Languages
C/C++ | Python | Go | Java | Rust
Databases
MySQL | PostgreSQL | MongoDB | DynamoDB| Redis
Tools
Wireshark | Snort | Suricata | TensorFlow | Apache Kafka | Docker
3rd–party cloud platforms
Amazon Web Services (AWS) | Microsoft Azure | Google Cloud Platform (GCP) | IBM Cloud | Oracle Cloud | Bosch IoT Suite
Frameworks and technologies
Multithreading | FPGA-based acceleration | Data plane development kit (DPDK) | Programmable network interfaces
Network virtualisation
Abstraction of network resources from the physical infrastructure which leads to increased flexibility, scalability, and security.
Application virtualisation
Isolation of applications from the operating system and hardware which results in improved portability, deployment, and security.
Server and storage virtualisation
Division of physical servers and storage into multiple virtual machines which enhances resource efficiency, scalability, and fault tolerance.
We Work With

Startups
We assist startups in the development of DPI software solutions by providing engineering teams to address specific challenges, fill resource gaps, and accelerate the growth of the business.

Enterprises
We provide DPI software development services for the telecom industry, internet service providers, healthcare institutions, financial organisations, and other types of businesses.

Tech Partners
We can be your reliable technology partner, by building DPI solutions tailored to your objectives. Our team is ready to become an integral part of your project.
Why Promwad
Network expertise
We provide end-to-end network design services through our in-depth knowledge of network technologies, protocols, and configurations for routers, switches, firewalls, and other devices.
Focus on security
We implement robust security protocols, including access control, multi-factor authentication, encryption, and other advanced security measures, in order to safeguard against potential threats.
Cutting-edge DPI
We use custom FPGAs, IEEE 1588 synchronisation, ARM processors, and Intel architecture in the rapid development of solutions while maintaining the infrastructure's scalability. Our AI team handles encrypted traffic and threat detection.
Our Engagement Models
Time & Material
– Payments for actual hours worked
– Regular reporting of time and results
– Regular communication with the team
– Connecting/disconnecting engineers upon request
– Flexible development processes
Dedicated Team
– Fixed monthly costs
– Custom-built team with specific competencies
– Fully dedicated engineering team
– Comprehensive IT infrastructure
– Maximum efficiency for complex projects
Project-Based
– Budget control
– Reduced risk
– Flexible resource allocation
– Clear scope
– Predictable timeline
– Quality control
Our Case Studies in the Telecom Industry
Do you need a quote for your DPI software development?
Drop us a line about your project! We will contact you today or the next business day. All submitted information will be kept confidential.
FAQ
How can DPI analyse encrypted traffic?
Deep Packet Inspection software solutions allow users to analyse encrypted traffic by decrypting it using various techniques, such as SSL/TLS interception. This process involves terminating the SSL/TLS session at the network security device and then analysing the decrypted content.
DPI inspects the content and applies analysis methods to identify patterns, signatures, or behaviours that indicate potential security threats or policy violations.
Can DPI machine learning adapt and evolve to new network traffic patterns and emerging threats?
DPI machine learning can certainly do that. By continuously training on large datasets, algorithms learn and recognise new patterns and anomalous behaviours, which allows DPI to stay up-to-date with evolving threats and adapt its detection capabilities accordingly.
What key challenges and limitations does DPI technology help overcome?
- handling encrypted traffic,
- managing high-speed networks with large volumes of data,
- ensuring accuracy in traffic classification,
- dealing with false positives or negatives,
- respecting privacy concerns associated with deep inspection of network traffic.
Are there any regulatory considerations or legal implications related to DPI deployment?
Yes, we should consider the legal aspects when deploying DPI. Deep packet inspection involves traffic analysis and can potentially access sensitive information. Therefore, it's critical to ensure compliance with local laws and regulations, such as GDPR in Europe and CCPA in the US, and obtain necessary consents or permissions when handling sensitive user data.
How does DPI contribute to network performance optimisation and bandwidth management?
Deep Packet Inspection solutions provide detailed insights into network traffic patterns and application usage. For example, DPI software can identify and prioritise real-time traffic, such as video conferencing and VoIP, over non-real-time traffic, such as file downloads. With this information, organisations can prioritise critical applications, implement quality of service (QoS) policies, optimise bandwidth allocation, and identify and manage bandwidth-intensive applications or protocols that may impact overall infrastructure performance.
How can organisations effectively integrate DPI into their existing network infrastructure?
Companies should evaluate their specific security and performance needs to seamlessly integrate Deep Packet Inspection software and hardware into the existing IT infrastructure.
This process involves:
- Understanding network architecture and components.
- Identifying suitable deployment points based on traffic patterns and security requirements.
- Assessing scalability and performance needs for efficient implementation.
- Taking hardware and software requirements and configuration into consideration during development and implementation.
- Ensuring interoperability with existing network components.
- Integrating the solution with existing security tools for enhanced DPI network security.
- Incorporating the solution into existing network management systems for centralised operation and DPI network monitoring.
- Providing training and support to administrators and users.
- Conducting periodic assessments and updates to optimise performance and adapt to network changes.








