Cybersecurity in Action: Lessons from the Frontlines


By Denis Petronenko,
Head of Telecom Unit at Promwad
Think your devices are safe? Think again. Hackers aren’t just after bank accounts and classified data – they’re targeting everything from smart beds to cars, doorbells, and industrial systems. If it’s connected to the internet, it’s a potential gateway for cyber threats.
Could your device be the next target? In this article, we will observe the most hackable embedded devices and expose the risks they pose to your personal and professional environments. These high-profile hacks made headlines and cost companies dearly for neglecting cybersecurity measures.
Table of contents
Case #1: The Smart Bed That Spied on You
Case #2: When Hackers Came Knocking: The Ring Breach
Case #3: The Nortek Nightmare: When Vendors Ignore Vulnerabilities
Case #4: Operation Salt Typhoon: Telecom Networks Under Siege
Case #5: The Jeep Hack That Shocked the World
Case #6: Stuxnet: The First Cyberweapon
Case #7: Meris Botnet: DDoS at an Unprecedented Scale
Case #1: The Smart Bed That Spied on You
Last year, Arizona developer Dillan Mills gained root access to a Sleep Number smart bed. His shocking discovery? The bed was sending user data back to the manufacturer without consent. This wasn’t an isolated case – it’s a wake-up call.

Prices for Sleep Number smart beds range from $999 to $5,499, but the manufacturer not guaranteed safety at this price point. Photo: Sleep Number Corporation
The implications go beyond privacy violations. Embedded systems often lack strong encryption protocols, making it easier for malicious actors to intercept and manipulate data. Ignoring the security of embedded devices can lead to data theft, privacy breaches, financial loss, and even life-threatening injuries.
This breach could have been easily avoided by implementing fundamental cybersecurity practices, such as:
- Data privacy by design. Ensure user consent for data collection and encrypt all transmitted data.
- Regular security audits. Periodic reviews of firmware and communication protocols to identify potential vulnerabilities.
- Timely security updates. Ensure devices receive timely firmware updates to mitigate risks.
Case #2: When Hackers Came Knocking: The Ring Breach
Hackers infiltrated Ring doorbells and home monitoring systems of 15 families, using weak, default passwords to access live feeds and even communicate with users through their devices. Beyond the invasion of privacy, these breaches created psychological distress for the victims, some of whom were harassed by the intruders.
Since then, all Ring users have been advised to add shared users to their accounts rather than sharing login details, change strong passwords regularly, and use two-factor authentication.
Such breaches could have been prevented through several key security measures, including:
- Stronger authentication. Implement multi-factor authentication (MFA) to reduce the risk of unauthorised access.
- Enforce credential changes. Enforce the ability to change default credentials with strong, complex passwords.
- Anomaly detection. Implement systems to detect anomalous activity, which can help identify and prevent suspicious actions.
Case #3: The Nortek Nightmare: When Vendors Ignore Vulnerabilities
Nortek Linear eMerge E3 devices had critical vulnerabilities. Despite knowing about them, the vendor delayed releasing patches, leaving thousands exposed to credential theft, malware, and DoS attacks. The vendor was aware of these vulnerabilities but failed to provide patches for quite some time, resulting in tens of thousands of complaints in 100 countries.
The Nortek IoT breach shows how quickly hackers can exploit connected IoT smart devices for attacks. It highlights the importance of proactively identifying and fixing vulnerabilities before cybercriminals exploit them.
This problem could have been mitigated with proactive security practices such as:
- Secure сommunication. Implement end-to-end encryption for data transmission to protect authentication credentials from interception.
- Patch management. Establish protocols for fast deploying security patches once vulnerabilities are identified and enable devices to receive updates automatically to ensure timely application of critical security fixes.
- Continuous threat monitoring. Continuously monitor and respond to new threats and vulnerabilities, maintaining detailed logs to facilitate rapid incident response.
Case #4: Operation Salt Typhoon: Telecom Networks Under Siege
A hacking group linked to Chinese intelligence infiltrated major US telecom networks, accessing sensitive data from over a million people, including political figures like President-elect Donald Trump and Vice President-elect J.D. Vance.
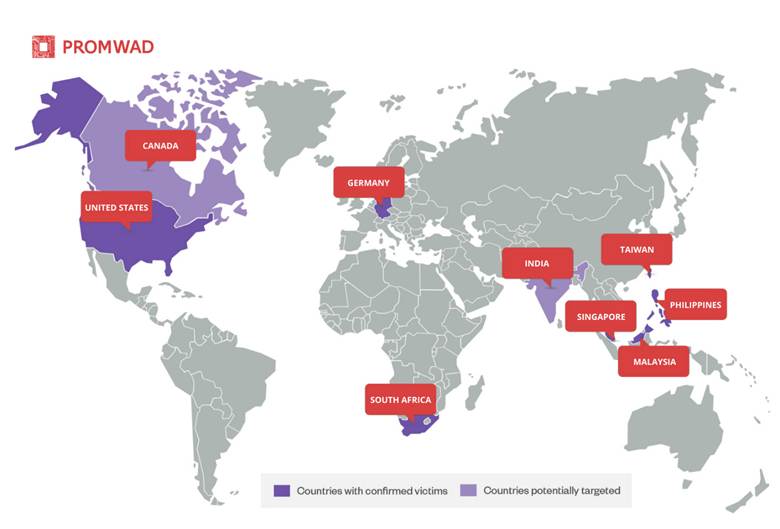
Countries affected or potentially affected by Salt Typhoon hacking group
The breach lasted 18 months, during which attackers posed as system engineers to avoid detection, transferring stolen data worldwide before routing it to China.
Implementing the following strategies could have significantly reduced the impact of this breach:
- Zero-trust networks. No device or user is inherently trusted, with continuous authentication and verification.
- Strict access control. Limit admin privileges, enforce multi-factor authentication, and regularly audit access logs to detect unauthorised activities.
- Advanced threat detection. Deploy tools to identify unusual patterns of behavior indicative of advanced persistent threats (APTs).
Case #5: The Jeep Hack That Shocked the World
Researchers Charlie Miller and Chris Valasek remotely controlled a Jeep Cherokee by exploiting vulnerabilities in its infotainment system. They took over the brakes, steering, and transmission from 10 miles away, demonstrating how modern vehicles' increasing reliance on software can expose them to life-threatening cyber risks.

One of the hacked model Jeep Grand Cherokee (WL) 4xe, a plug-in hybrid SU combines off-road capability with electrified efficiency. Source: Wikimedia Commons, Photo by M 93, CC BY-SA 4.0
This attack could have been prevented by embedding security into the development lifecycle through:
- Secure software development. Regular code audits and penetration tests to identify and mitigate vulnerabilities before exploitation.
- Network isolation. Physically and logically separate safety-critical systems from less critical components like infotainment.
- Access controls. Enforce robust authentication protocols and role-based access control (RBAC).
Case #6: Stuxnet: The First Cyberweapon
Stuxnet, a sophisticated worm, targeted Iranian nuclear facilities, causing physical destruction through cyber means. This attack changed the cybersecurity landscape forever. It exploited zero-day vulnerabilities, manipulated industrial control systems, and operated undetected for months, showcasing the devastating potential of cyber warfare.

Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon by journalist Kim Zetter focuses on the first and to this day the largest specialised attack on industrial systems
Critical infrastructure attacks like this could be thwarted with measures such as:
- Segmented networks. Enhance physical and logical isolation of critical systems from external networks, limiting malware spread.
- Strict access control. Enforce multi-factor authentication and minimize the number of users with administrative access.
- Proactive monitoring. Deploy intrusion detection and prevention systems to monitor suspicious activity.
Case #7: Meris Botnet: DDoS at an Unprecedented Scale

The MikroTik hEX series, an enterprise-class router line used by ISPs and network administrators, was targeted in the attack. Source: mikrotik.com
In 2021, the Meris botnet used unsecured MikroTik devices to launch DDoS attacks, peaking at 22 million requests per second. The attacks targeted high-profile organizations like Yandex and Cloudflare, demonstrating the vulnerability of poorly secured networking devices.
Preventive actions that could have mitigated this threat include:
- Device hardening. Enforce strong passwords, reduce the attack surface by disabling unnecessary services, and deploy firewalls.
- Network defense. Implement rate limiting, firewall rules, and DDoS mitigation strategies.
- Incident response planning. Maintain detailed logs of network activity to facilitate rapid incident response and forensic analysis.
Case #8: VPNFilter Malware: The Global Router Infiltration

Linksys and Netgear routers shown to demonstrate common networking solutions
VPNFilter infected over 500,000 devices, including MikroTik, Linksys, and Netgear routers. The malware allowed attackers to monitor network traffic, steal credentials, and even disable devices remotely. Its persistence mechanisms made it particularly difficult to eradicate.
Such widespread infections could have been prevented with:
- Firmware updates. Regularly update devices to patch known vulnerabilities, enabling automatic updates where possible to reduce delays in patch deployment.
- Network monitoring. Use IDS/IPS systems to detect suspicious activity.
- Incident response. In the event of an infection, reboot devices, perform factory resets, and collaborate with security organizations for mitigation.
Why It Matters: The Hidden Cost of Ignoring Cybersecurity
Cyberattacks on IoT devices aren’t just about stolen data. They can cripple businesses, ruin reputations, and even endanger lives. Whether you're a tech giant or a small startup, ignoring cybersecurity is not an option. The financial repercussions can be staggering, including regulatory fines, legal liabilities, and loss of customer trust.
Promwad Cybersecurity Services for Your Devices & Software
Strengthen your solutions with our expertise in cybersecurity. Whether you're building a new product or upgrading an existing one, we ensure robust protection at every stage:
- Compliance audits. Assess your device or service against cybersecurity standards.
- Cybersecurity by design. Integrate security from the ground up.
- Threat analysis. Identify and mitigate potential vulnerabilities.
- Hardening services. Secure hardware, firmware, applications, and networks.
- Penetration testing. Simulate real-world attacks to fortify your defenses.
- DevSecOps. Integrating security practices into the DevOps pipeline.
Don’t Wait to Become the Next Headline!
Promwad's cybersecurity experts help you identify vulnerabilities before hackers do. We don’t just spot problems – we fix them.
Secure your devices and protect your business today!








