IIoT & Industrial Ethernet Security: How to Ensure Safety with New IIoT Sensors & Predictive Maintenance

Industrial facilities are among the top five most vulnerable targets for cyberattacks that could result in production stoppage, equipment breakdown worth several millions of dollars, blackouts, or sensitive information leaks. Let’s discusses the top cyber risks and how to prevent them.
With the rise of IIoT and Industry 4.0, industrial ethernet security has become particularly acute because connecting parts of industrial networks to the Internet and cloud services brings not only business value but also additional risks.
The possibility of these risks was shown in the famous movie Live Free or Die Hard (Die Hard 4.0 outside North America) starring Bruce Willis. In the story, cyber-terrorists take out the country's critical facilities. The intruders gain remote access to the traffic control system and unplug it, thereby wreaking chaos on the city's streets. Note: to shut down a central power plant, they had to go directly to this facility and connect to the systems from the inside!
That's how it worked in 2007 when Die Hard was released, and that's how it works now that OPC UA (IEC 62541) for secure data transmission within industrial networks is already widely implemented. There is still no reason for engineers to connect basic enterprise control nodes to the Internet for remote access to industrial networks.
However, there are examples of evading industrial it security not only in movies but also in real life, where attackers have managed to inflict significant damage on businesses:
- In 2010, one of the most famous industrial attacks occurred when the Stuxnet virus hit more than a thousand centrifuges at a uranium enrichment plant in Iran.
- In 2002, the corporate computers of employees at PDVSA, a Venezuelan oil company, were attacked. As a result, oil production was reduced from 3 million to 370,000 barrels per day.
- In 2014, attackers disabled a steel mill in Germany using a phishing attack to gain access to the furnace control system and hack into its shutdown mechanisms.
Large-scale attacks of this kind are infrequent, but their impact is critical to production, which is why not only individual companies but entire industry groups are addressing the issue.
In 2022, the OPC Foundation, PI, ODVA and FieldComm Group, leaders in security standards development, announced the first joint Industrial Ethernet Security Harmonization Group (IESHG) document. It summarises the basics of cyber security in industrial automation: risks, trends, security certifications, how to deal with vulnerabilities and general security provisions.
Industrial network architecture & industrial cyber security: an overview of the basic units
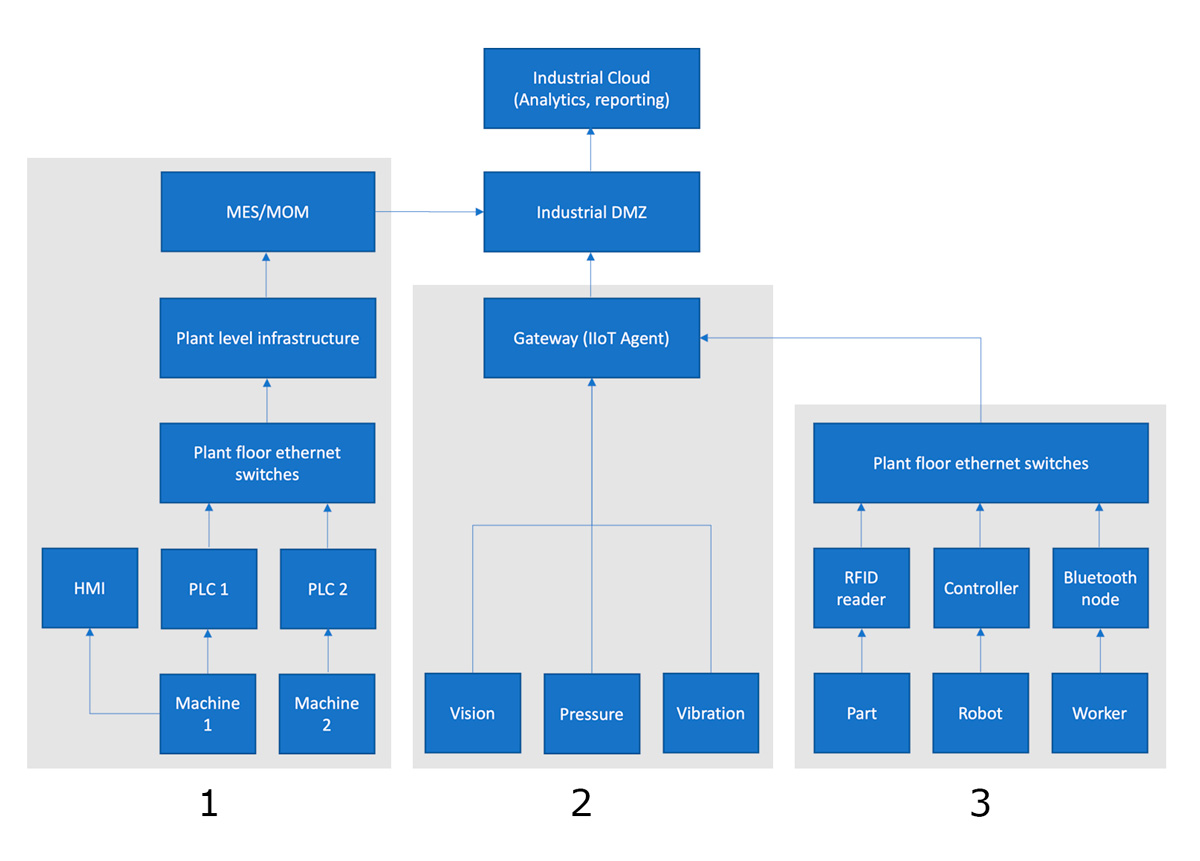
Example of a cloud-oriented industrial architecture from Industrial Cybersecurity Case Studies and Best Practices by International Society of Automation (gca.isa.org)
The diagram above shows an example of a network architecture for an industrial enterprise that uses cloud services. Let's look at it in detail, unit by unit (framed in grey), to understand better the truthful scenario of the Die Hard 4.0 movie we mentioned above.
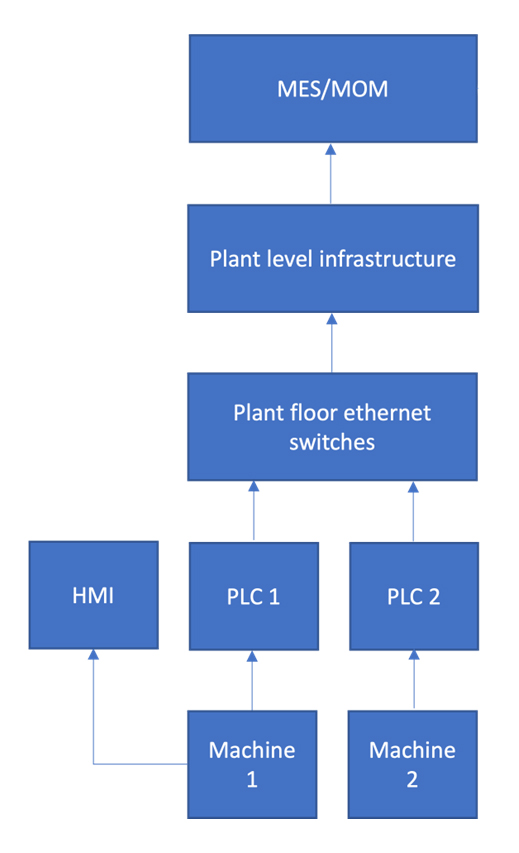
Unit 1. Production process management via MES or MOM
Unit 1 is the autonomous control of the production process. It involves machines and other industrial equipment with HMIs and controllers (PLCs) connected to plant floor Ethernet switches in an enterprise-wide infrastructure. This entire network and its equipment are managed and controlled locally at the MES or MOM level (Manufacturing Execution System or Manufacturing Operations Management).
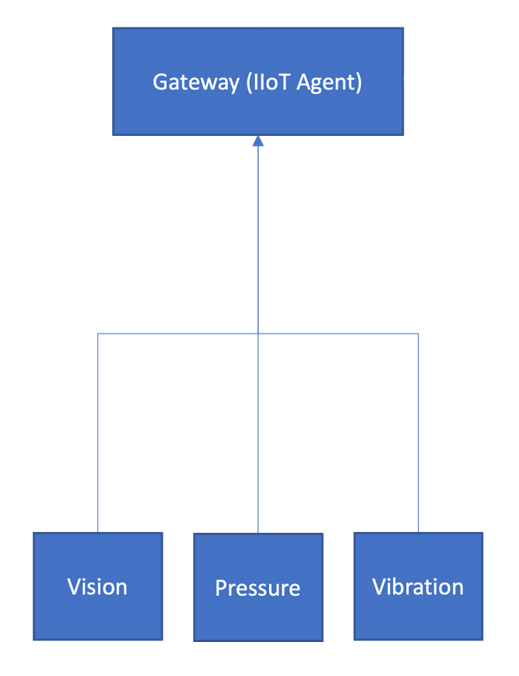
Unit 2. Data transfer from sensors to the industrial cloud via an IIoT gateway
Unit 2 is the IIoT network that includes various sensors connected to the IIoT gateway. The data from these sensors is eventually transmitted to the industrial cloud for reporting and analysis. Thanks to cloud computing and other cloud services, industrial enterprises can implement visual monitoring, collect data for predictive maintenance, automatically generate orders for necessary purchases, etc. Unit 2 is not directly related to the production process management (Unit 1), so secure access to the Internet is acceptable. This is where IIoT brings real value to business.
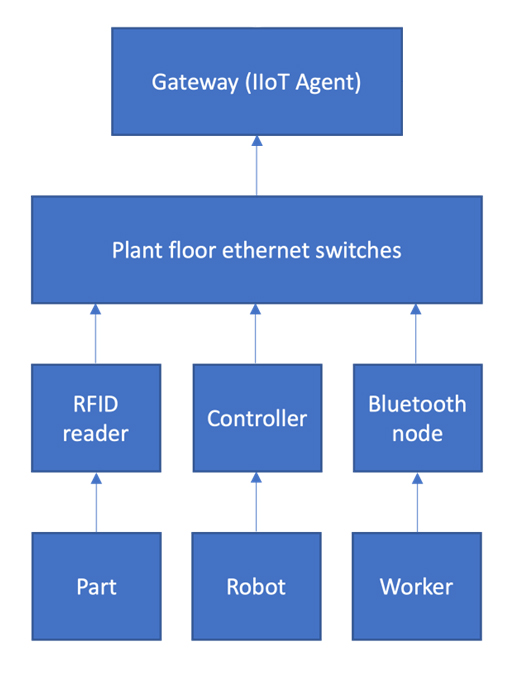
Unit 3. Transferring the status of industrial equipment to the industrial cloud via an IIoT gateway
Unit 3 is the collection of data about materials, industrial robots/machines and workers in production. This information is transmitted by RFID readers, controllers and Bluetooth nodes. The collected data is sent to the IIoT gateway.
As you can see, units 2 and 3 are the most vulnerable part of the process, as this is where the IIoT gateway (and cloud services) comes in.

All three units in a cloud-oriented industrial architecture with industrial DMZ which separates the industrial network components from the Internet
The data from all three blocks is transmitted to the Industrial DMZ (demilitarised zone), a special component for cybersecurity that divides the industrial network into different zones. The DMZ is an intermediate point between the enterprise and the rest of the public Internet. It protects internal network resources against vulnerabilities while transferring permitted information to the cloud server.
As you can see from the typical example we explored above, the production processes are organised over local industrial networks without access to the Internet. Even if a cloud-oriented infrastructure with IIoT is used, all collected information is not transmitted directly to the cloud but via an Industrial DMZ, which only allows specific traffic to pass through. The machine control remains within the local MES or MOM, making it impossible for intruders to remotely connect to the production process.
Thus, the emergence of IIoT in industrial automation and the electric power industry can take advantage of advanced information analysis for management decisions without putting key processes at risk and ensuring industrial cyber security — if the network architecture is planned intelligently.
Attack targets and cyber security best practices
Let's review the main problem areas in the internal enterprise network and ways to ensure industrial ethernet security:
Vulnerability of wireless communications. Ethernet APL for secure data transmission
Many wireless transmission protocols are vulnerable and can undermine industrial cyber security — each protocol can suffer up to 5 vulnerabilities per month. When data transmission is deployed over long distances, attackers can access the transmission airwaves and affect process control, leading to equipment failure or even explosions.
This risk can be reduced to zero by implementing Ethernet APL, a two-wire technology for industrial Ethernet networks (EtherNet/IP, HART-IP, OPC UA and PROFINET).
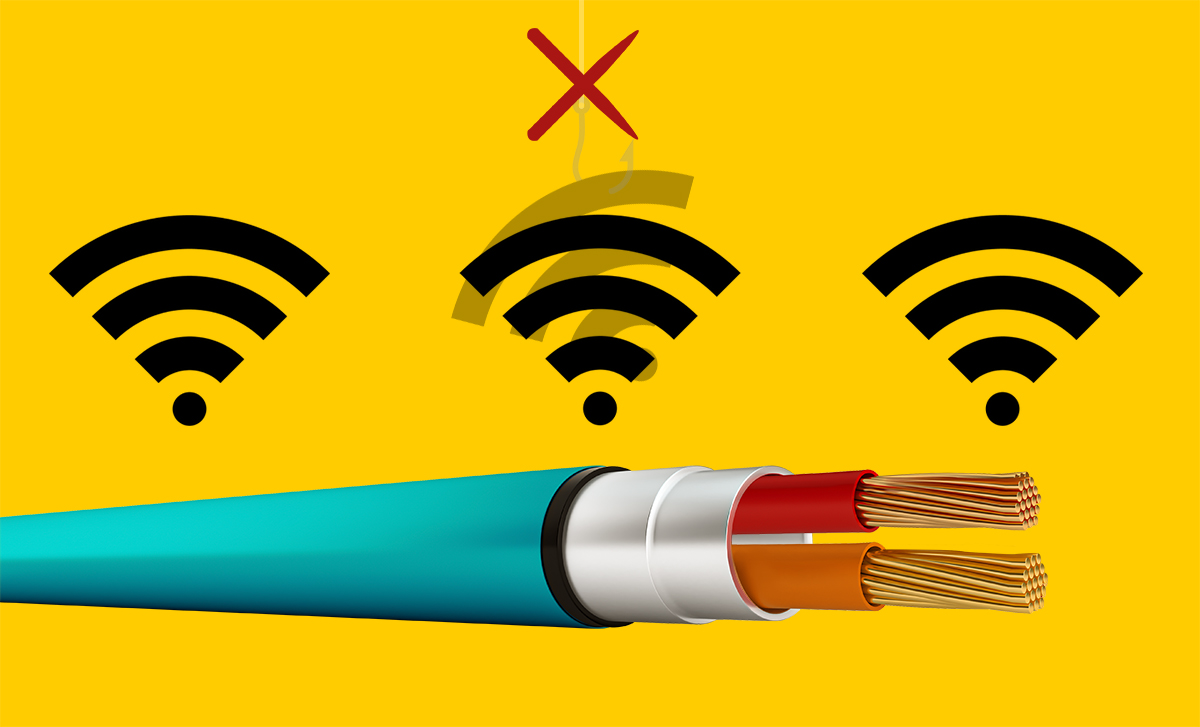
Industrial Ethernet APL two-wire transmission eliminates the risk of data interception over the airwaves
An essential advantage of Ethernet APL is that data transfer and power supply to devices take place over the same cable. Here are a few key features of the technology:
- high bandwidth: 10 Mbit/sec;
- laying of networks over long distances – up to 1,000 m, and branch lines – up to 200 m;
- use in hazardous areas;
- the combined operation of devices from different manufacturers;
- flexible and scalable network topology.
Considering that the Ethernet APL cables are used for both power and data transmission, there is no need to use a wireless connection, as you will, in any case, need a cable to power your devices. So why transmit data over the air, exposing the risk of intrusion and increasing vulnerability?
Vulnerable IIoT sensors and gateway. Dividing the infrastructure with Industrial DMZ
Another risk area for the cyber security of industrial automation and control systems is data transmission from sensors to the cloud, which is implemented via an IIoT gateway. In this case, it will be necessary to secure the backend or frontend side if the data is transmitted to the cloud. There is a possible solution: to divide the network infrastructure into separate blocks and secure each with an Industrial DMZ.
Some industries use smart or IIoT sensors that implement the necessary AI algorithms to pre-process the data and send it directly to the cloud. The same security principles apply to standard sensors and the IIoT gateway. Judging from our practice, these smart sensors are still relatively rare. Implementing AI algorithms is always more expensive. Therefore, many companies prefer a more low-cost option: the development of industrial sensors that work in tandem with a standard controller.
The IIoT unit (sensors and gateway) is usually responsible for process monitoring and predictive maintenance. It is not involved in the control of industrial equipment. Its vulnerability could harm this part of the business process but not the production itself.
Vulnerabilities in the OPC UA protocol. TLS/SSL and other security methods
The OPC UA and MQTT protocols responsible for data transfer in industrial networks will be vulnerable without using encryption technologies such as SSL and TSL, which create a secure channel between a client and a server.
Open Platform Communications Unified Architecture (OPC UA) is a communication protocol for exchanging data between various systems and devices in industrial automation. OPC UA supports transport protocols such as MQTT and works across multiple network topologies.
A key feature of OPC UA is its security architecture, which provides end-to-end encryption and authentication for data confidentiality, integrity and availability. It uses standard security technologies, including SSL/TLS encryption.
Secure Sockets Layer (SSL) and Transport Layer Security (TLS ) are cryptographic protocols that enable secure communications over the Internet. TLS is the successor to SSL and is considered more reliable because it uses stronger encryption algorithms, enhanced key exchange protocols, and message authentication codes.
The IESHG document published by Industrial Ethernet Security Harmonization Group has basic information about the importance of these certificates and public-key.
One of the frequent attacks on OPC UA is flooding. An intruder sends many requests to a server in a short period. This attack is difficult to detect because the requests and messages may appear legitimate. Flooding drains the server's resources and makes it unable to process requests from the client, disrupting systems and devices that use the attacked OPC UA.
There are several ways to protect against flooding attacks on OPC UA:
- network segmentation to isolate the OPC UA server from other networks and limit access to it;
- limiting the number of requests during a certain period will help the server to handle incoming traffic better and avoid being overloaded;
- monitoring network traffic and looking for strange patterns that may indicate a flooding attack.
Another option for attacking OPC UA is man-in-the-middle. In this attack, the intruder gains access to the data exchange process between the client and the server. It allows either transferring the data to be altered or stealing sensitive information.
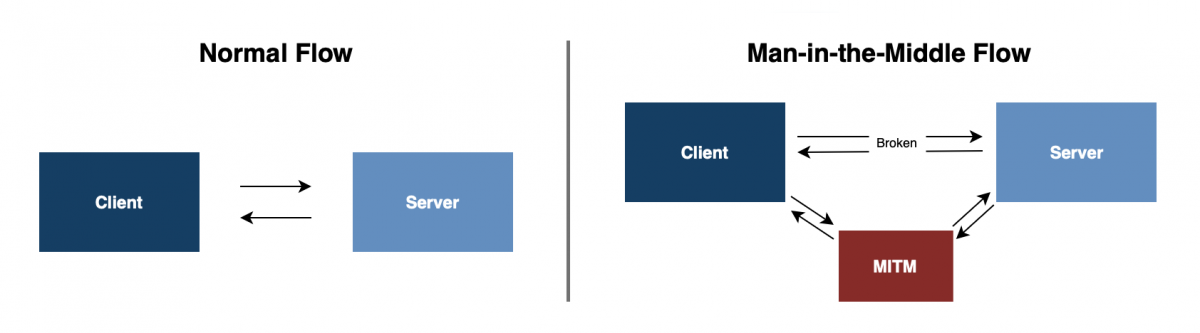
A scheme of the "man-in-the-middle" attack on OPC UA
Encryption methods and digital authentication certificates, network segmentation, secure communication channels such as VPNs, and security protocol updates protect against this attack.
PLC vulnerability and how to protect controllers
Intruder access to programmable logic controllers (PLCs) can lead to industrial process disruption and physical damage and threaten the personal safety of employees.
Cybercriminals can use PLCs to attack engineering workstations — applications configuring and maintaining PLCs. These stations are an important and often vulnerable link that contains process information and gives access to other PLCs. A standard scenario for this attack looks like this:
- Intruders gain initial access to a PLC and create a fake fault.
- An engineer connects to the hacked PLC through the workstation to fix the problem and thus accesses the application through the infected PLC.
- The engineering workstation can infiltrate the internal network and other systems and disrupt the logic of other PLCs.
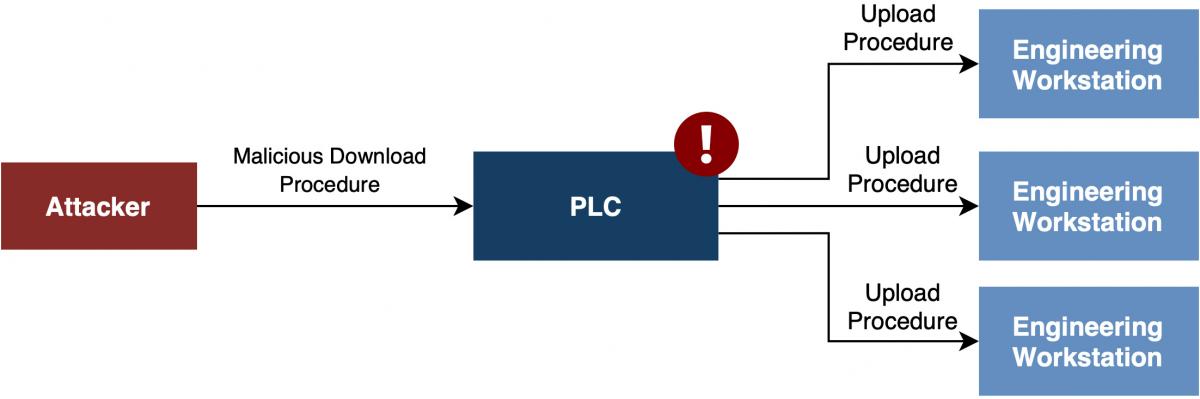
This is what a PLC attack looks like: by hacking into one PLC and gaining access to an engineering station, attackers can control an entire network of PLCs at a production facility
If the final target of an attack is a systems integrator's workstation, then intruders could gain access to all PLCs managed by that integrator, which could be dozens of organisations worldwide.
How to protect PLCs:
- Limit physical access to PLCs.
- Segment networks: separate the industrial network from other networks and grant PLC access to selected engineering stations.
- Regulate PLC access with engineering station authentication and verification mechanisms.
- Use public key infrastructure (PKI) to help encrypt traffic between client and server (engineering station and PLC).
- Monitor network traffic: data is uploaded and downloaded when a PLC is attacked. It can be a marker of hacking if it occurs outside the context of normal PLC operation.
Attacks on SCADA systems and how to protect them

Attacks on SCADA systems can physically damage critical infrastructure and disrupt plant operations. Network segmentation, access control, and implementation of an intrusion detection system can reduce vulnerability
SCADA (Supervisory Control and Data Acquisition) system can be attacked through the following vulnerabilities:
- The lack of a restriction certificate in the Modbus protocol, which is often used in SCADA systems. This vulnerability allows intruders to infiltrate the data transmission process and access messages and legitimate addresses, eventually influencing production processes.
- The lack of authority and access control allows users to execute any command. To avoid this, users must be divided into groups with different levels of access.
- No encryption when sending data by ICS / SCADA protocols.
- The request-response scheme of Modbus and DNP3 protocols also makes them susceptible to denial-of-service attacks, as a slave station can send data to an unauthorised master station, increasing the risk of this attack.
Promwad's expertise in the design of secure solutions for industrial Ethernet
Commissioned by our clients, we design hardware and develop software for industrial solutions and efficient production processes. These projects cannot be realised without industrial security services, which include several components:
- Development of devices and embedded systems: we design IIoT gateways, frequency converters, PLCs, drive units and sensors.
- Software solutions for Ethernet security: we implement security protocols, applying our knowledge of cryptography and providing symmetrical and asymmetrical data encryption.
By developing Ethernet-APL-based solutions, we help our clients to ensure stable and secure equipment operation — with new analytical and predictive maintenance capabilities. Our designs include APL field and power switches based on the latest solutions from Analog Devices and Texas Instruments.
According to the analysis of feedback, our customers appreciate Promwad's ability to give an objective assessment of new technologies, break through the information noise and choose the best engineering solutions for their business needs. Promwad helps clients save time and money on implementation, without sacrificing security or chasing fancy solutions.
At Promwad, we work with the best practices for deploying secure hardware and software systems for industrial automation, robotics, and the electric power industry. Contact us if you need an engineering partner!