How Promwad Ensures Cybersecurity with Tor Bridges and Obfs4 Protocol
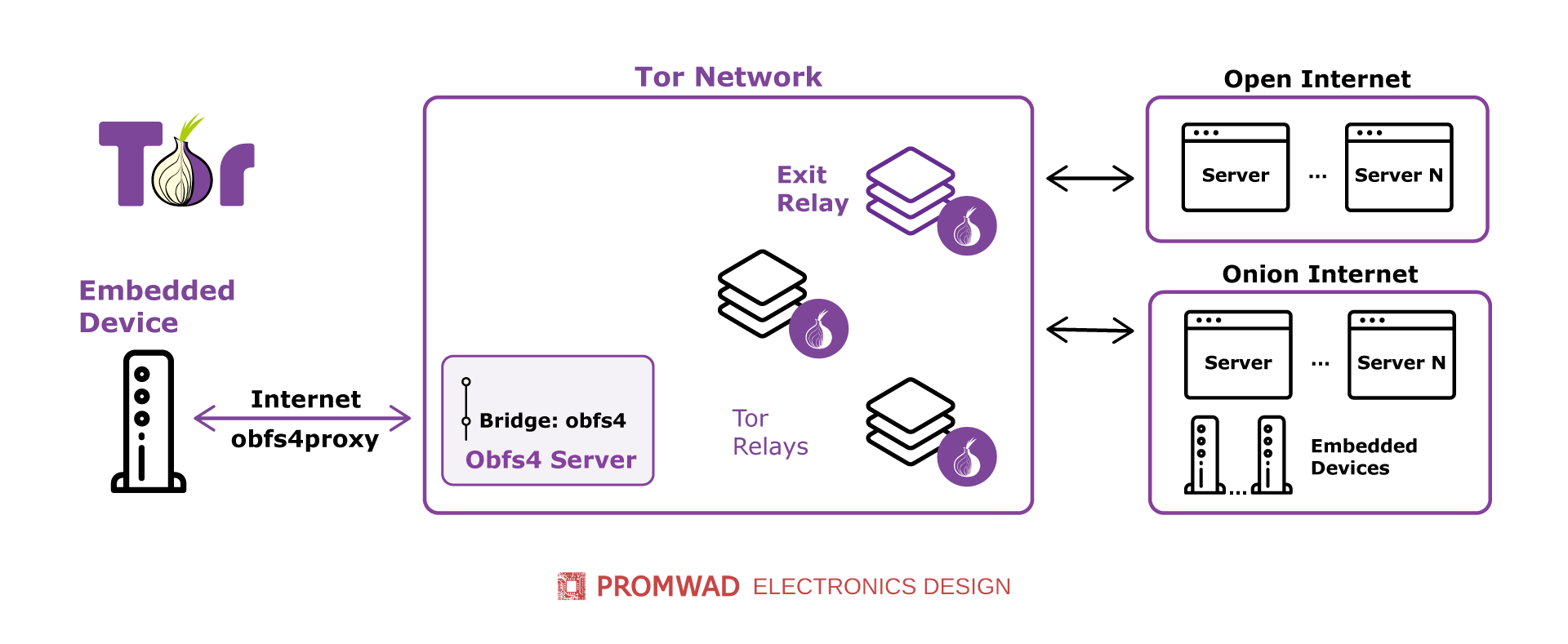
Tor Bridges with Obfs4. A use case with an embedded device

We implemented a Tor Bridge in our client’s engineering project to ensure its corporate data privacy and security in a distributed network of offices and remote employees worldwide. And thanks to the obfs4 protocol, we provided an additional level of protection against traffic interception. This cyber security solution can bring real value to our clients in the corporate and telecom sectors.
How it works
The Tor network (The Onion Router) was created to provide anonymity and avoid Internet censorship. It is legal in most countries, but individual countries or organisations restrict its use. And Tor Bridges arose as a response to these restrictions.
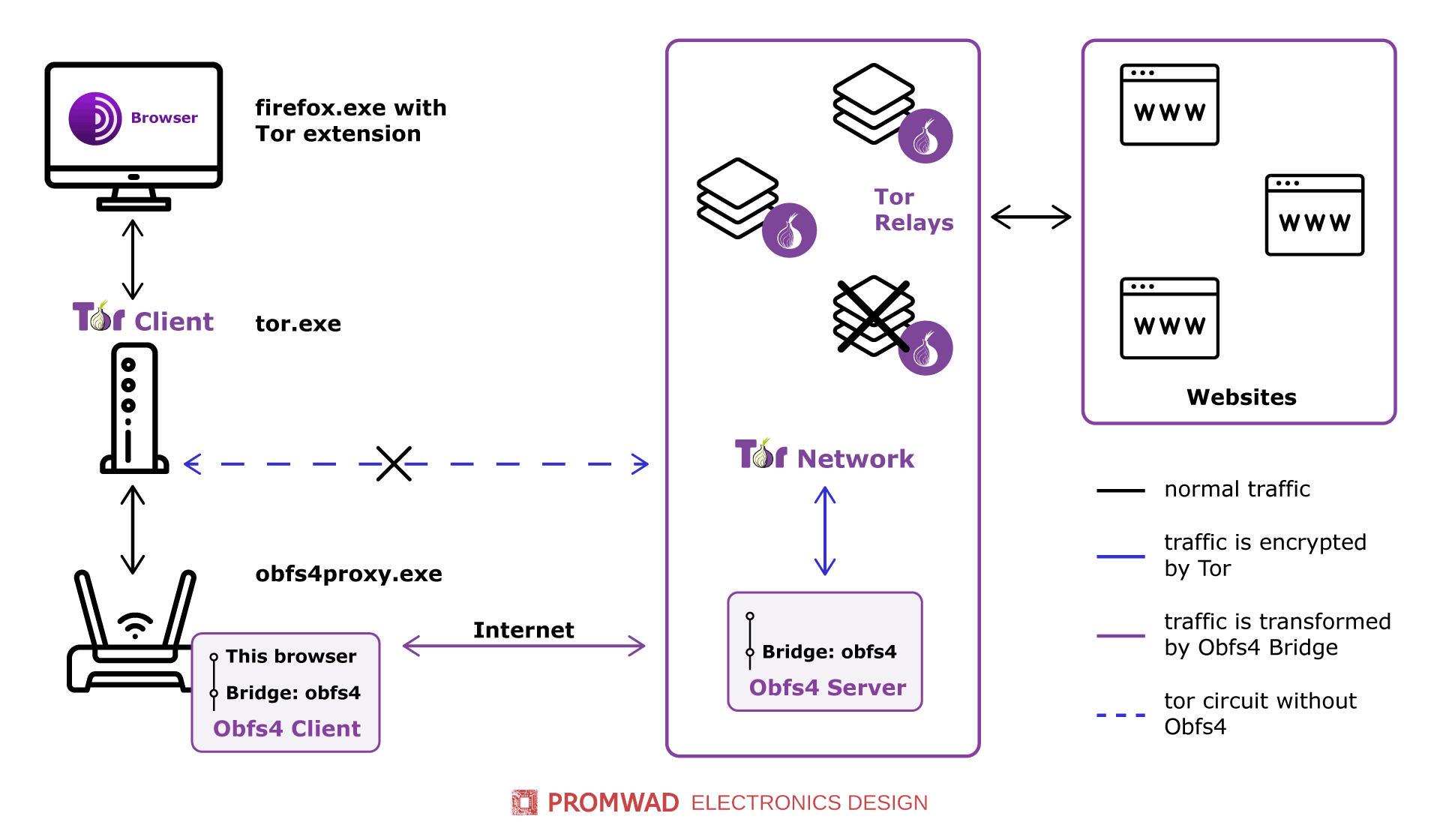
The general scheme of operation of Tor Bridges with Obfs4 client
Here are the main advantages of these bridges:
- Obfuscation is a method of changing the program code while keeping its functions. It makes Tor traffic look like regular 'unsecured' traffic.
- Hiding users' IP addresses for an extra layer of privacy and anti-surveillance. The Tor bridge address is displayed instead of the user's IP address.
- Bridge IP dynamism. Bridges change their IP addresses and configuration to make it harder for sensors to detect them.
However, censors and cybercriminals have learned to identify conventional Tor bridges over time. And Tor bridges with the obfs4 transport protocol have become a response to this threat. Obfs4 adds an extra layer of obfuscation, making it even more difficult to identify connections.
Use cases of cybersecurity management services withTor bridges & obfs4
Tor bridges and obfs4 protocols empower our clients with corporate data protection features and completely anonymous internet access. Outside of the secure network, it will be impossible to identify not only the number of users worldwide but even the location of their corporate server. We provide these features by connecting to the Tor network via a SOCKS (Socket Secure) proxy server on embedded devices. This ensures the anonymity of all internet traffic, not just web traffic sent over HTTP/HTTPS.
We also can integrate Tor Bridges with obfuscating pluggable transports, including obfs4, in our clients’ embedded solutions.
- Ensuring corporate data security. Obfs4-enabled Tor bridges ensure confidentiality and prevent instances of surveillance or leakage of critical corporate information.
- Securing remote access to corporate resources. It is especially important when employees work remotely or access internal systems from external networks.
- Accessing blocked resources. Bridges allow employees of international companies to access resources that may be blocked in some countries.
- Combating cybercrime. Secure bridges help with attack investigations, malware research, cyber threat intelligence and cyber defence solutions testing.
Secure connections, like any tool, can be used for various purposes. However, we see this technology primarily as a tool for securing and preserving corporate data privacy. We are open to cooperating with companies needing cybersecurity consulting services or engineering support to develop its it-managed security services.
Feel free to contact us to discuss your engineering challenges in telecom:












